Java Persistence With Hibernate Ebook Pdf Download
High-Performance Java Persistence
Spring Persistence with Hibernate, Second Edition has been updated to cover Spring Framework version 4 and Hibernate version 5. After reading and using this book, you’ll have the fundamentals to apply these persistence solutions into your own mission-critical enterprise Java applications that you build using Spring. Java Persistence with Hibernate Christian Bauer, Gavin King, Gary Gregory pdf. EPUB - MOBI Java Persistence with Hibernate download ebook PDF EPUB,.
High-Performance Java Persistence
Get the most out of your persistence layer
A high-performance data access layer must resonate with the underlying database system. Knowing the inner workings of a relational database and the data access frameworks in use can make the difference between a high-performance enterprise application and one that barely crawls.
This book is 100% complete
Completed on 2019-05-05
PackagesDetails
Java Persistence With Hibernate Second Edition
EU customers: Price excludes VAT.
VAT is added during checkout.
For the ultimate learning experience, you should definitely enroll in my
High-Performance Java Persistence video courses.
If you're interested in a print copy, then check out the Paperback version on Amazon,Amazon.co.uk, Amazon.de or Amazon.fr.
This book is a journey into Java data access performance tuning. From connection management, to batch updates, fetch sizes and concurrency control mechanisms, it unravels the inner workings of the most common Java data access frameworks.
The first part aims to reduce the gap between application developers and database administrators. For this reason, it covers both JDBC and the database fundamentals that are of paramount importance when reducing transaction response times. In this first part, you'll learn about connection management, batch updates, statement caching, result set fetching and database transactions.
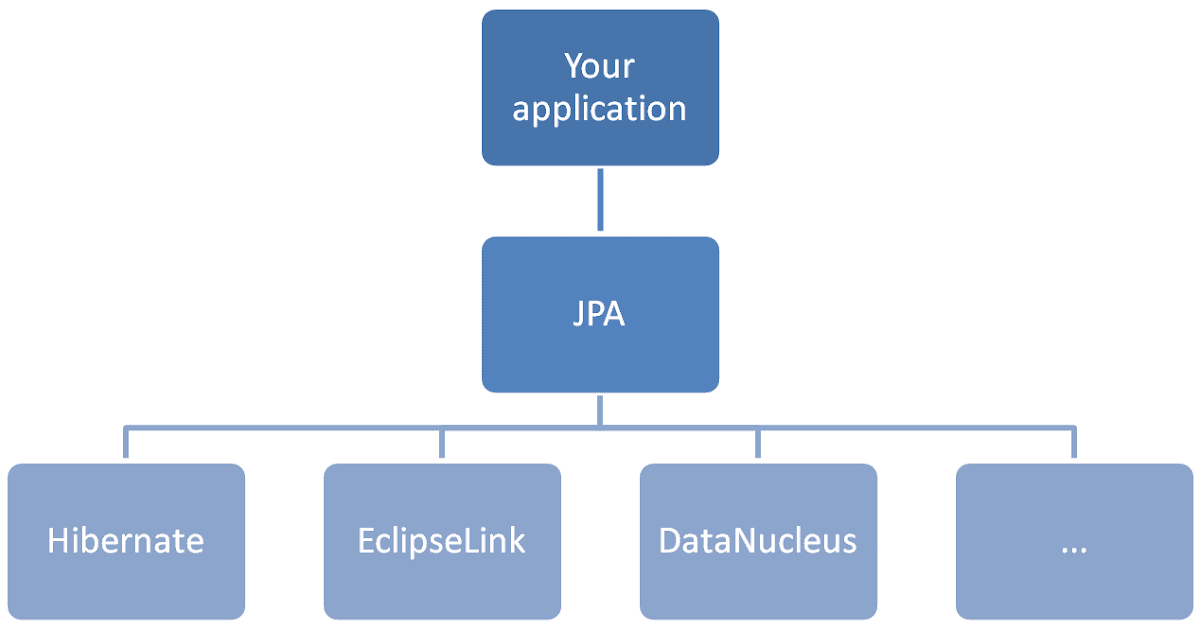
The second part demonstrates how you can take advantage of JPA and Hibernate without compromising application performance. In this second part, you'll learn about the most efficient Hibernate mappings (basic types, associations, inheritance), fetching best practices, caching and concurrency control mechanisms.
The third part is dedicated to jOOQ and its powerful type-safe querying capabilities, like window functions, common table expressions, UPSERT, stored procedures and database functions.
25% discount - Pack of 3
This package is for 3 copies of the 'High-Performance Java Persistence' at a 25% discount.
English
PDF
EPUB
MOBI
APP
Working With Hibernate Java Persistence
Reader Testimonials
Lukas Eder
Java Champion, founder and CEO of Data Geekery GmbH, the company behind jOOQ
This book is a must-read for everyone aiming to push their relational databases to the limit with their Java application.
Rafael Winterhalter
Java Champion, creator of Byte Buddy
There is no resource that better summarizes the performance implications of using JDBC, either directly or via JPA and Hibernate. If you are talking to a database on the JVM, add this book to your reading shelf.
Markus Eisele
Java Champion, Developer Advocate at Lightbend
Muscle manual by nikita vizniak physical medicine. In addition, this text is a valuable study guide for students, practitioners and doctors preparing for National Board Exams, State/Province Board Exams, Clinical Skills Examinations and many other standardized licensure examinations.
Object to database mapping is one of the core requirements in many Java EE related projects. And the available frameworks make it easy for their users to get started. But as soon as you hit particular requirements around distributed transactions or performance you realise how much database and framework knowledge is required to implement them. Vlad made his insane experience available in an easy-to-read book. If you are dealing with JPA or Hibernate, this book is a must read.
Antonio Goncalves
Java Champion, co-creator of AllCraft.io

Writing a book is difficult, but writing a book about performance and persistence is a real challenge. If you want to understand how locking, sharding, replication, database concurrency control work, then this book is for you. Vlad gives you plenty of tips and tricks on Hibernate, helping you diagnose your performance issues (e.g. mapping, fetching, or caching). I learn a lot by reading his book and I highly recommend it if you use relational databases and ORM tools such as Hibernate.
Eugen Paraschiv
Owner of Baeldung, Spring courses author
Good books on persistence are few and far between. This is something else - it's deeply researched but also entirely practical. I'm basically using it as a reference for everything SQL. Plus, the transaction chapter is a must read.
Simeon Malchev
Software engineer & enthusiast, creator of Vibur DBCP
This book is a highly recommended resource for every developer who is serious about learning and mastering the difficult topic of designing and implementing high performance Java database applications. The book covers in detail the performance aspect of the plain JDBC and Hibernate programming, explains the theoretical and practical implications of the database transactions, and discusses some rare topics such as the database connection pool sizing and statement caching.

- Preface
- The database server and the connectivity layer
- The application data access layer
- The ORM framework
- The native query builder framework
- Video Course
- Testimonials
- Preface
- I JDBC and Database Essentials
- 1. Performance and Scaling
- 1.1 Response time and throughput
- 1.2 Database connections boundaries
- 1.3 Scaling up and scaling out
- 1.3.1 Master-Slave replication
- 1.3.2 Multi-Master replication
- 1.3.3 Sharding
- 2. JDBC Connection Management
- 2.1 DriverManager
- 2.2 DataSource
- 2.2.1 Why is pooling so much faster?
- 2.3 Queuing theory capacity planning
- 2.4 Practical database connection provisioning
- 2.4.1 A real-life connection pool monitoring example
- 2.4.1.1 Concurrent connection request count metric
- 2.4.1.2 Concurrent connection count metric
- 2.4.1.3 Maximum pool size metric
- 2.4.1.4 Connection acquisition time metric
- 2.4.1.5 Retry attempts metric
- 2.4.1.6 Overall connection acquisition time metric
- 2.4.1.7 Connection lease time metric
- 2.4.1 A real-life connection pool monitoring example
- 3. Batch Updates
- 3.1 Batching Statements
- 3.2 Batching PreparedStatements
- 3.2.1 Choosing the right batch size
- 3.2.2 Bulk processing
- 3.3 Retrieving auto-generated keys
- 3.3.1 Sequences to the rescue
- 4. Statement Caching
- 4.1 Statement lifecycle
- 4.1.1 Parser
- 4.1.2 Optimizer
- 4.1.2.1 Execution plan visualization
- 4.1.3 Executor
- 4.2 Caching performance gain
- 4.3 Server-side statement caching
- 4.3.1 Bind-sensitive execution plans
- 4.4 Client-side statement caching
- 4.1 Statement lifecycle
- 5. ResultSet Fetching
- 5.1 ResultSet scrollability
- 5.2 ResultSet changeability
- 5.3 ResultSet holdability
- 5.4 Fetching size
- 5.5 ResultSet size
- 5.5.1 Too many rows
- 5.5.1.1 SQL limit clause
- 5.5.1.2 JDBC max rows
- 5.5.1.3 Less is more
- 5.5.2 Too many columns
- 5.5.1 Too many rows
- 6. Transactions
- 6.1 Atomicity
- 6.2 Consistency
- 6.3 Isolation
- 6.3.1 Concurrency control
- 6.3.1.1 Two-phase locking
- 6.3.1.2 Multi-Version Concurrency Control
- 6.3.2 Phenomena
- 6.3.2.1 Dirty write
- 6.3.2.2 Dirty read
- 6.3.2.3 Non-repeatable read
- 6.3.2.4 Phantom read
- 6.3.2.5 Read skew
- 6.3.2.6 Write skew
- 6.3.2.7 Lost update
- 6.3.3 Isolation levels
- 6.3.3.1 Read Uncommitted
- 6.3.3.2 Read Committed
- 6.3.3.3 Repeatable Read
- 6.3.3.4 Serializable
- 6.3.1 Concurrency control
- 6.4 Durability
- 6.5 Read-only transactions
- 6.5.1 Read-only transaction routing
- 6.6 Transaction boundaries
- 6.6.1 Distributed transactions
- 6.6.1.1 Two-phase commit
- 6.6.2 Declarative transactions
- 6.6.1 Distributed transactions
- 6.7 Application-level transactions
- 6.7.1 Pessimistic and optimistic locking
- 6.7.1.1 Pessimistic locking
- 6.7.1.2 Optimistic locking
- 6.7.1 Pessimistic and optimistic locking
- 1. Performance and Scaling
- II JPA and Hibernate
- 7. Why JPA and Hibernate matter
- 7.1 The impedance mismatch
- 7.2 JPA vs. Hibernate
- 7.3 Schema ownership
- 7.4 Entity state transitions
- 7.5 Write-based optimizations
- 7.6 Read-based optimizations
- 7.7 Wrap-up
- 8. Connection Management and Monitoring
- 8.1 JPA connection management
- 8.2 Hibernate connection providers
- 8.2.1 DriverManagerConnectionProvider
- 8.2.2 C3P0ConnectionProvider
- 8.2.3 HikariCPConnectionProvider
- 8.2.4 DatasourceConnectionProvider
- 8.2.5 Connection release modes
- 8.3 Monitoring connections
- 8.3.1 Hibernate statistics
- 8.3.1.1 Customizing statistics
- 8.3.1 Hibernate statistics
- 8.4 Statement logging
- 8.4.1 Statement formatting
- 8.4.2 Statement-level comments
- 8.4.3 Logging parameters
- 8.4.3.1 DataSource-proxy
- 8.4.3.2 P6Spy
- 9. Mapping Types and Identifiers
- 9.1 Types
- 9.1.1 Primitive types
- 9.1.2 String types
- 9.1.3 Date and Time types
- 9.1.4 Numeric types
- 9.1.5 Binary types
- 9.1.6 UUID types
- 9.1.7 Other types
- 9.1.8 Custom types
- 9.2 Identifiers
- 9.2.1 UUID identifiers
- 9.2.1.1 The assigned generator
- 9.2.2 The legacy UUID generator
- 9.2.2.1 The newer UUID generator
- 9.2.3 Numerical identifiers
- 9.2.3.1 Identity generator
- 9.2.3.2 Sequence generator
- 9.2.3.3 Table generator
- 9.2.3.4 Optimizers
- 9.2.3.4.1 The hi/lo algorithm
- 9.2.3.4.2 The default sequence identifier generator
- 9.2.3.4.3 The default table identifier generator
- 9.2.3.4.4 The pooled optimizer
- 9.2.3.4.5 The pooled-lo optimizer
- 9.2.3.5 Optimizer gain
- 9.2.3.5.1 Sequence generator performance gain
- 9.2.3.5.2 Table generator performance gain
- 9.2.3.6 Identifier generator performance
- 9.2.1 UUID identifiers
- 9.1 Types
- 10. Relationships
- 10.1 Relationship types
- 10.2 @ManyToOne
- 10.3 @OneToMany
- 10.3.1 Bidirectional
@OneToMany - 10.3.2 Unidirectional
@OneToMany - 10.3.3 Ordered unidirectional
@OneToMany- 10.3.3.1 @ElementCollection
- 10.3.4 @OneToMany with @JoinColumn
- 10.3.5 Unidirectional
@OneToManySet
- 10.3.1 Bidirectional
- 10.4 @OneToOne
- 10.4.1 Unidirectional
@OneToOne - 10.4.2 Bidirectional
@OneToOne
- 10.4.1 Unidirectional
- 10.5 @ManyToMany
- 10.5.1 Unidirectional
@ManyToMany - 10.5.2 Bidirectional
@ManyToMany - 10.5.3 The
@OneToManyalternative
- 10.5.1 Unidirectional
- 11. Inheritance
- 11.1 Single table
- 11.1.1 Data integrity constraints
- 11.2 Join table
- 11.3 Table-per-class
- 11.4 Mapped superclass
- 11.1 Single table
- 12. Flushing
- 12.1 Flush modes
- 12.2 Events and the action queue
- 12.2.1 Flush operation order
- 12.3 Dirty Checking
- 12.3.1 The default dirty checking mechanism
- 12.3.1.1 Controlling the Persistence Context size
- 12.3.2 Bytecode enhancement
- 12.3.1 The default dirty checking mechanism
- 13. Batching
- 13.1 Batching insert statements
- 13.2 Batching update statements
- 13.3 Batching delete statements
- 14. Fetching
- 14.1 DTO projection
- 14.1.1 DTO projection pagination
- 14.1.2 Native query DTO projection
- 14.2 Query fetch size
- 14.3 Fetching entities
- 14.3.1 Direct fetching
- 14.3.1.1 Fetching a Proxy reference
- 14.3.1.2 Natural identifier fetching
- 14.3.2 Query fetching
- 14.3.3 Fetching associations
- 14.3.3.1 FetchType.EAGER
- 14.3.3.2 FetchType.LAZY
- 14.3.3.2.1 The N+1 query problem
- 14.3.3.2.2 How to catch N+1 query problems during testing
- 14.3.3.2.3 LazyInitializationException
- 14.3.3.2.4 The Open Session in View Anti-Pattern
- 14.3.3.2.5 Temporary Session Lazy Loading Anti-Pattern
- 14.3.3.3 Associations and pagination
- 14.3.4 Attribute lazy fetching
- 14.3.5 Fetching subentities
- 14.3.1 Direct fetching
- 14.4 Entity reference deduplication
- 14.5 Query plan cache
- 14.1 DTO projection
- 15. Caching
- 15.1 Caching flavors
- 15.2 Cache synchronization strategies
- 15.2.1 Cache-aside
- 15.2.2 Read-through
- 15.2.3 Write-invalidate
- 15.2.4 Write-through
- 15.2.5 Write-behind
- 15.3 Database caching
- 15.4 Application-level caching
- 15.4.1 Entity aggregates
- 15.4.2 Distributed key-value stores
- 15.4.3 Cache synchronization patterns
- 15.4.4 Synchronous updates
- 15.4.5 Asynchronous updates
- 15.4.5.1 Change data capture
- 15.5 Second-level caching
- 15.5.1 Enabling the second-level cache
- 15.5.2 Entity cache loading flow
- 15.5.3 Entity cache entry
- 15.5.3.1 Entity reference cache store
- 15.5.4 Collection cache entry
- 15.5.5 Query cache entry
- 15.5.6 Cache concurrency strategies
- 15.5.6.1 READ_ONLY
- 15.5.6.1.1 Inserting READ_ONLY cache entries
- 15.5.6.1.2 Updating READ_ONLY cache entries
- 15.5.6.1.3 Deleting READ_ONLY cache entries
- 15.5.6.2 NONSTRICT_READ_WRITE
- 15.5.6.2.1 Inserting NONSTRICT_READ_WRITE cache entries
- 15.5.6.2.2 Updating NONSTRICT_READ_WRITE cache entries
- 15.5.6.2.3 Risk of inconsistencies
- 15.5.6.2.4 Deleting NONSTRICT_READ_WRITE cache entries
- 15.5.6.3 READ_WRITE
- 15.5.6.3.1 Inserting READ_WRITE cache entries
- 15.5.6.3.2 Updating READ_WRITE cache entries
- 15.5.6.3.3 Deleting READ_WRITE cache entries
- 15.5.6.3.4 Soft locking concurrency control
- 15.5.6.4 TRANSACTIONAL
- 15.5.6.4.1 XA_Strict mode
- 15.5.6.4.2 XA mode
- 15.5.6.4.3 Inserting TRANSACTIONAL cache entries
- 15.5.6.4.4 Updating TRANSACTIONAL cache entries
- 15.5.6.4.5 Deleting TRANSACTIONAL cache entries
- 15.5.6.1 READ_ONLY
- 15.5.7 Query cache strategy
- 15.5.7.1 Tablespace query cache invalidation
- 15.5.7.2 Native SQL statement query cache invalidation
- 16. Concurrency Control
- 16.1 Hibernate optimistic locking
- 16.1.1 The implicit optimistic locking mechanism
- 16.1.1.1 Resolving optimistic locking conflicts
- 16.1.1.2 Splitting entities
- 16.1.1.3 Versionless optimistic locking
- 16.1.1.3.1 OptimisticLockType.DIRTY update caveat
- 16.1.1 The implicit optimistic locking mechanism
- 16.2 The explicit locking mechanism
- 16.2.1 PESSIMISTIC_READ and PESSIMISTIC_WRITE
- 16.2.1.1 Lock scope
- 16.2.1.2 Lock timeout
- 16.2.2 LockModeType.OPTIMISTIC
- 16.2.2.1 Inconsistency risk
- 16.2.3 LockModeType.OPTIMISTIC_FORCE_INCREMENT
- 16.2.4 LockModeType.PESSIMISTIC_FORCE_INCREMENT
- 16.2.1 PESSIMISTIC_READ and PESSIMISTIC_WRITE
- 16.1 Hibernate optimistic locking
- 7. Why JPA and Hibernate matter
- III JOOQ
- 17. Why jOOQ matters
- 17.1 How jOOQ works
- 17.2 DML statements
- 17.3 Java-based schema
- 17.4 Upsert
- 17.4.1 Oracle
- 17.4.2 SQL Server
- 17.4.3 PostgreSQL
- 17.4.4 MySQL
- 17.5 Batch updates
- 17.6 Inlining bind parameters
- 17.7 Complex queries
- 17.8 Stored procedures and functions
- 17.9 Streaming
- 17.10 Keyset pagination
- 17. Why jOOQ matters
The Leanpub 45-day 100% Happiness Guarantee
Within 45 days of purchase you can get a 100% refund on any Leanpub purchase, in two clicks.
See full terms
Free Updates. Free App. DRM Free.
If you buy a Leanpub book, you get free updates for as long as the author updates the book! Many authors use Leanpub to publish their books in-progress, while they are writing them. All readers get free updates, regardless of when they bought the book or how much they paid (including free).
Most Leanpub books are available in PDF (for computers), EPUB (for phones and tablets), MOBI (for Kindle) and in the free Leanpub App (for Mac, Windows, iOS and Android). The formats that a book includes are shown at the top right corner of this page.
Finally, Leanpub books don't have any DRM copy-protection nonsense, so you can easily read them on any supported device.